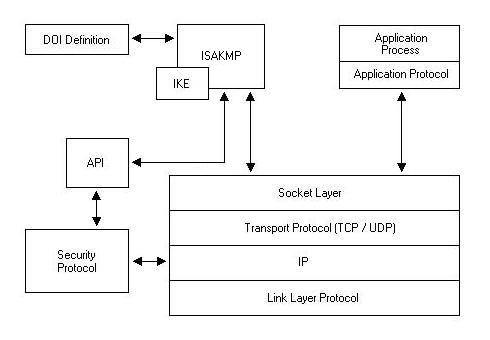
Imperfect Forward Secrecy: How Diffie-Hellman Fails in Practice | January 2019 | Communications of the ACM

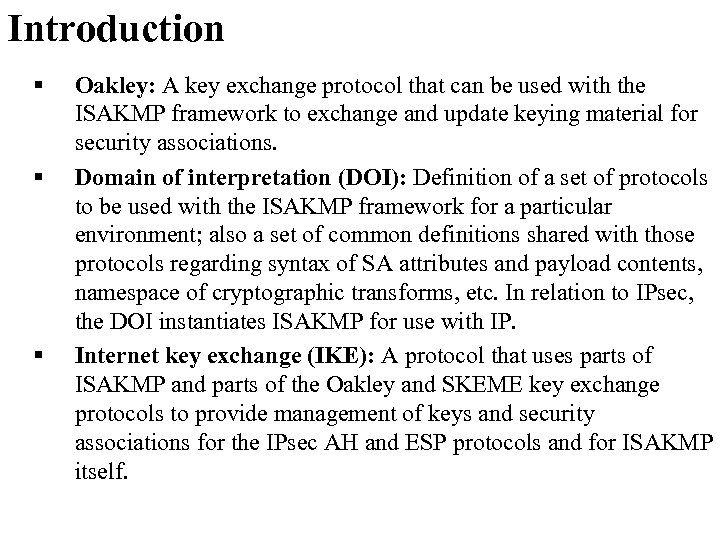
Computer Security and PGP: What Is Diffie - Hellman Key Exchange Protocol or Oakley Protocol? | Computer security, Network sharing, Buddy

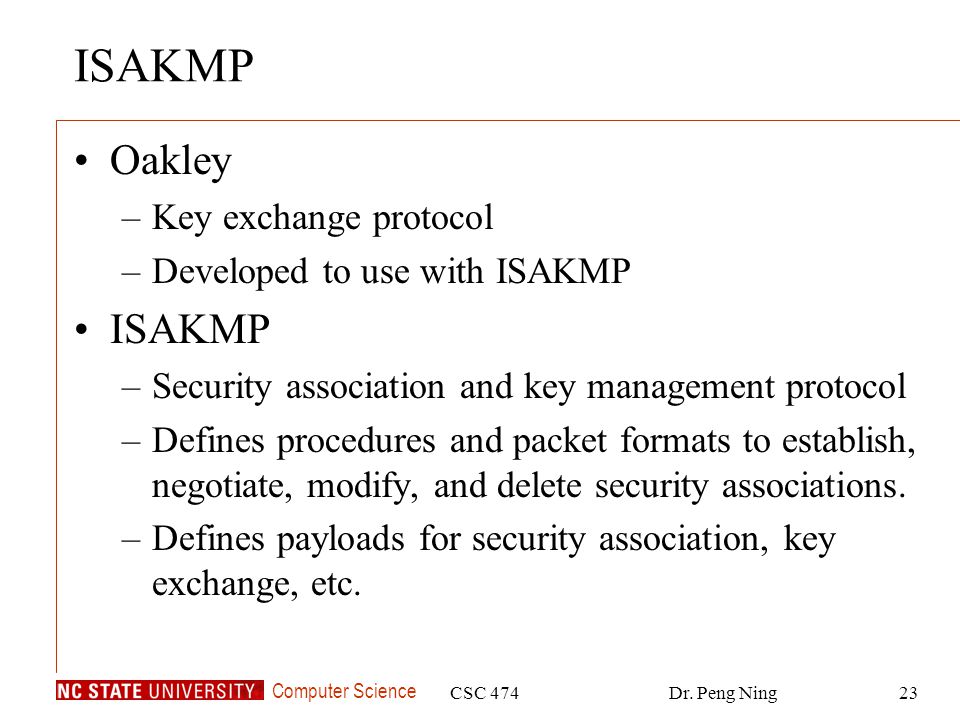
Resolution of ISAKMP/Oakley key-agreement protocol resistant against denial-of-service attack | Semantic Scholar

![Operation of SA other protocols: OAKLEY, SKEME and ISAKMP [8] [5].... | Download Scientific Diagram Operation of SA other protocols: OAKLEY, SKEME and ISAKMP [8] [5].... | Download Scientific Diagram](https://www.researchgate.net/profile/Riaz_Khan10/publication/297336095/figure/fig2/AS:558684922814464@1510212273166/ESP-Header-Format_Q320.jpg)



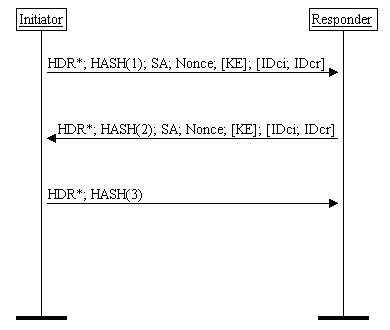





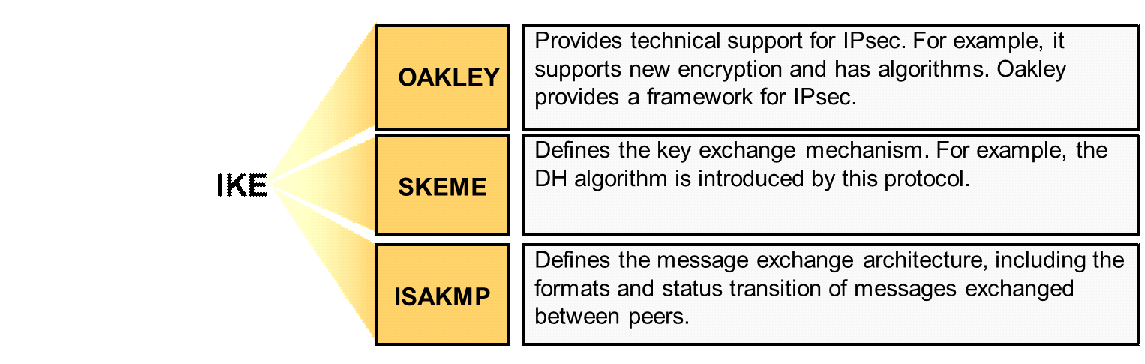
![Operation of SA other protocols: OAKLEY, SKEME and ISAKMP [8] [5].... | Download Scientific Diagram Operation of SA other protocols: OAKLEY, SKEME and ISAKMP [8] [5].... | Download Scientific Diagram](https://www.researchgate.net/profile/Riaz_Khan10/publication/297336095/figure/fig4/AS:558684922224640@1510212273285/Operation-of-SA-other-protocols-OAKLEY-SKEME-and-ISAKMP-8-5-OAKLEY-it-is-a-key_Q320.jpg)